
All-in-one plugin for Burp Suite for Java deserialization vulnerability detection and exploitation
Download Java-Deserialization-Scanner
JAva Deserialization Scanner is a Burp Suite plugin intended to detect and exploit Java deserialization vulnerabilities. It was written by Federico Dotta, Security Specialist at @ Mediaservice.net.
This plugin consists of three different components:
1. Integration with Burp Suite active and passive scanner
2. Manual tester, to detect Java deserialization vulnerability at custom insertion point
3.Exploiter, which allows to actively exploit Java deserialization vulnerabilities, using the yososial frohoff (https://github.com/frohoff/ysoserial)
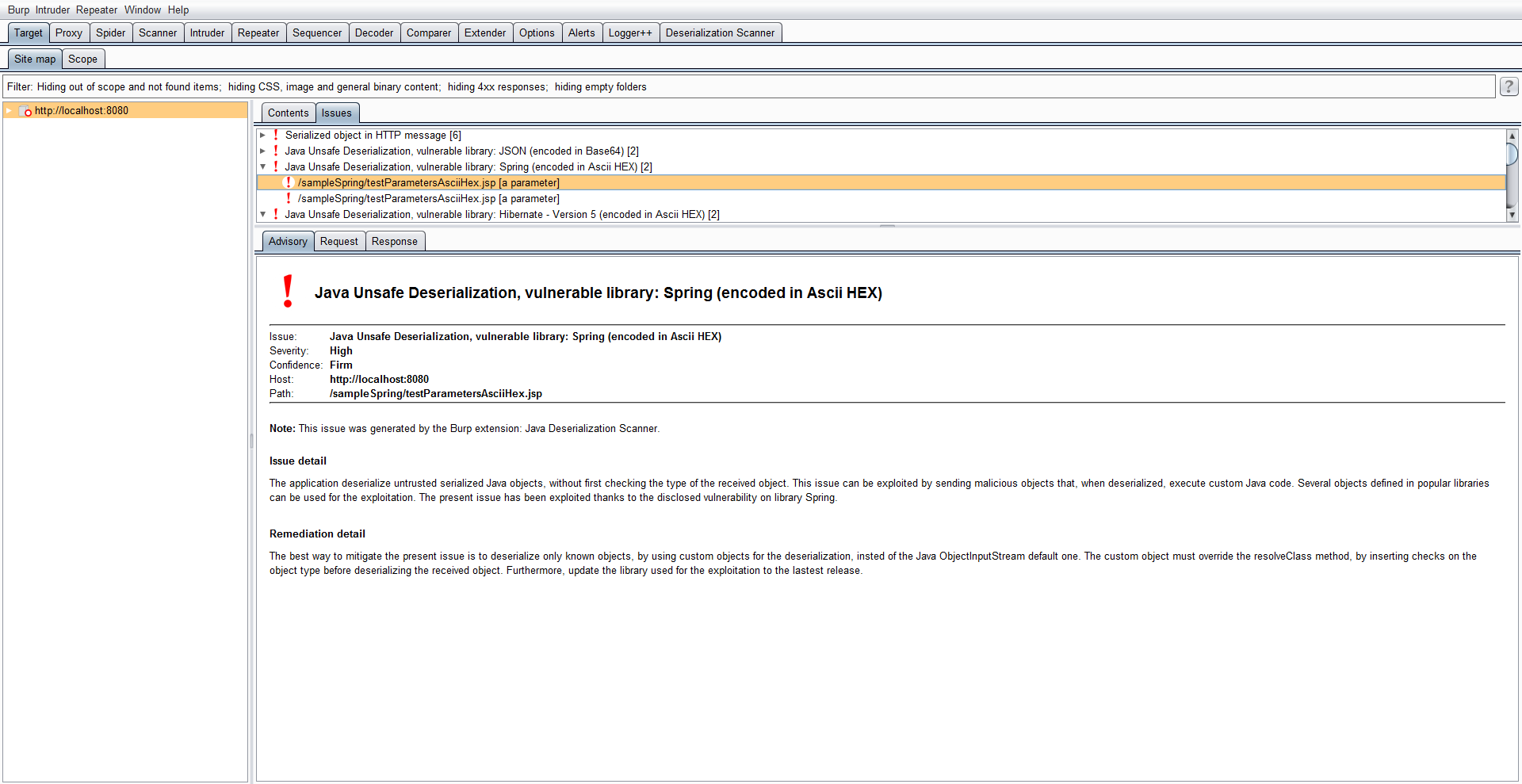
Integration with Burp Suite Scan active and passive
Java Deserialization Scanner uses custom payload generated with a modified version of "ysoserial", a tool created by frohoff and gebl, to detect Java's deserialization vulnerabilities. The native tool (https://github.com/frohoff/ysoserial) generates a charge for execution of commands on the system, using the Runtime.exec function. Usually, however, it is not possible to see the output of the command and as a result it is not easy to write the scanner based on this kind of function. The modified version adds the charge generation synchronous sleep function, it is useful to examine their problems otomatis.Saat the Java deserialization this, passive inspection of Java Deserialiation Scanner reports a serialized Java object in the HTTP request (in raw format or encoded in Base64 or Ascii Hex) and active checking actively scans weak deserialization functions along with the following weak library presence:- Apache Commons Collections 3 (up to 3.2.1), with three different chains
- Apache Commons Collections 4 (up to 4.4.0), with two different chains
- Spring (up to 4.2.2), with two different chains
- Java 6 and Java 7 (<= Jdk7u21) without any weak library
- Hibernate 5
- JSON
- Rome
Manual tester
This plugin offers a special tab for launching sleep-load detection at a custom insertion point, to check Java's deserialization vulnerabilities in certain situations where strange entry points do not allow detection with the scanner. The results of the manual testers can be included between the results of the Burp Suite scanner.Exploiter
After that Java deserialization vulnerability has been found, it is possible to actively exploit the problem with a special tab of Exploitation. The plugin makes it possible to configure the ysoserial frohoff path and use this tool to generate exploit payloads. The exploiter, like other components, supports three different encodings for the load: raw, Base64 or Ascii Hex.Screenshot
Installation
- Download Burp Suite: http://portswigger.net/burp/download.html
- Install Java Deserialization Scanner from the BApp Store or follow these steps:
- Download the last release of Java Deserialization Scanner
- Open Burp -> Extender -> Extensions -> Add -> Choose JavaDeserializationScannerXX.jar file
User Guide
- After installation, an active Java Deserialization Scanner and a passive check will be added to the Burp Suite scanner (it is possible to disable checks on the options tab)
- Just run the active or passive scanner to check also the weak Java deserialization
- With a special "Manual" tab it is possible to set the injection point and execute the attack with all its cargo
- With a special tab "Utilization", it allows to actively exploit Java deserialization vulnerabilities
- "Configuration" contains all the configurations required for correct plugin work










No comments:
Post a Comment